“Every great magic trick consists of three parts or acts. The first part is called “The Pledge.” The magician shows you something ordinary: a deck of cards, a bird or a man. He shows you this object. Perhaps he asks you to inspect it to see if it is indeed real, unaltered, normal. But of course… it probably isn’t.
The second act is called “The Turn.” The magician takes the ordinary something and makes it do something extraordinary. Now you’re looking for the secret… but you won’t find it, because of course you’re not really looking. You don’t really want to know. You want to be fooled. But you wouldn’t clap yet.
Because making something disappear isn’t enough; you have to bring it back. That’s why every magic trick has a third act, the hardest part, the part we call “The Prestige.” – Cutter
The Pledge
Intelligence covers a broad spectrum of disciplines in academia and generally functions to reduce the fog of war within the Department of Defense (DoD). Within the US intelligence community among the 16 primary agencies, intelligence has different scope, different definition.
Thus, when discussing any kind of intelligence it’s important to put it into the context of the agency and the scope. Are you referring to the Central Intelligence Agency (CIA)? If so, are you referring to the Department of Operations (DO)? Or the Department of Intelligence (DI)? At the CIA, for example, the DO is a function of intelligence; however in the DoD J3/G3/S3 or Operations is not a function of intelligence (J2/G2/S2). Operations would continue in the absence of intelligence (perhaps not as effectively) but they would continue.
Most of the time the interface for intelligence with operations in the DoD is the “Two Three” shop. The intelligence operations shop. Hypothetically, this is where Coriolanus meets Jack Murphy. The shop divides further, but that’s a topic for another day.
The Turn
The disciplines of intelligence are human intelligence (HUMINT) or what we classically think of as “spies”. Imagery Intelligence (IMINT) is combined with geographic information systems (GIS). Signals Intelligence (SIGINT), subcomponents of which are communications intelligence (COMINT) and electronic intelligence (ELINT); this is often the most time-sensitive of all the disciplines followed closely by HUMINT.
The most recent entry to our field is a direct result of 9/11, and one I very much appreciate. It is open source intelligence (OSINT). Open source intelligence is basically everything not available using national or military collection efforts. Academia, hard copy archives, media, metadata, data repositories, and blogs are just some examples.
So what brings it all these disciplines together? The fusion analyst.
To put it lightly, a good fusion analyst knows where the bodies are buried. He knows collectors by their collection code and often discusses their findings to gain insight into products. A good analyst knows operators and policy makers by name, meaning he needs to have a good doctrinal understanding of both policy and operations.
Much like one of the two most important lines on an OPORD (Operations Order), you must understand their intent. Despite their nomenclature each of the disciplines produces “data” and that data is a raw “scrape” or “collection effort”. It has not been vetted.
When a fusion analyst puts it together, it becomes “finished intelligence”, the end state of all the individual disciplines. As a fusion analyst I write “evals” on Intelligence Information Reports (IIR) and SIGINT reports, to determine their utility and refine the collections process. The final product is a “fusion” of all inputs into a brief, web page, papers, or network chart or all the above.
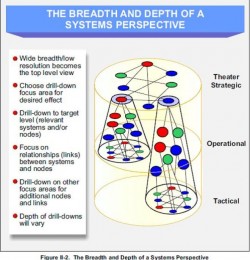
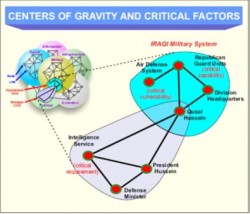
In military Intelligence, at the doctrinal joint level (much like Operations) enemy vulnerabilities are broken down using Clausewitz’s “center of gravity” (COG) concepts. This concept was further developed by Dr. Joe Strange, a former professor at the United States Marine Corps (USMC) war college, and last I heard, working at the Counter-IED Operations Integration Center (COIC) and is commonly referred to Systems of Systems Analysis (SoSA).
To understand military intelligence you need to have an intimate understanding of the seven elements of national power: Diplomatic, Information, Military, Economic, Financial, Intelligence, and Law Enforcement. These are all the elements a government can use to exercise its power over both its citizens and other nations.
The doctrinal methodology (as written in Joint Publication 2-0) for looking at DIMEFIL is the Joint Intelligence Processing of the Operational Environment (or JIPOE). This is used at an operational level and referred to as IPOE (or formerly intelligence processing of the battlespace (IPB)). It works hand in hand with the Joint Operational Planning and Execution System (JOPES).
In this analyst’s opinion, to understand your job most effectively you must know how operations work intimately at the tactical, operational, and strategic level. Only then will you be any good to a decision maker. JIPOE categorizes all COG’s into Political, Military, Economic, Social, Infrastructural, and Informational COG’s or PMESII. Notice how these correspond to the elements of national power. This is the relationship between capabilities and vulnerabilities.
What’s important to realize is that COG’s are determined in the “Risks, Assumptions, and Constraints” portion of operational planning. If a decision maker does not have enough information on a node or series of nodes in the COG, he designates this as a Commanders’ Critical Information Requirement (CCIR), and this is then used to build Priority Intelligence Requirements (PIRs). From a bottom up approach: mission, enemy, terrain and weather, troops and support available, time available, civil considerations (METT-TC) becomes IPOE and then this becomes JIPOE.
I am very familiar with tools like Palantir, DCGS-A, M3, etc. and I use all of them. However, that changes from top-down in the military hierarchy. I have all these tools here in CONUS (Continental United States) in a Sensitive Compartmented Information Facility (SCIF).
Once you leave the US and work in TSCIF (T is for tactical) or TOC, you run into bandwidth requirements. Often times at the tactical level I have only had one or two tools available, and then you have to rely on the operator’s and analyst’s best weapon…your brain. You have to create time wheels and CARVER charts from ground up. Not hard, but time-consuming and usually you are running against a clock that counts time in lives.
The Prestige
That’s doctrine. It’s important to understand doctrine… because you need to know it. Then you need to understand how to destroy it, how to make it yours and redevelop it. You need to approach a problem set deemed impossible and reduce it to ruins.
What you just learned was doctrinal intelligence.
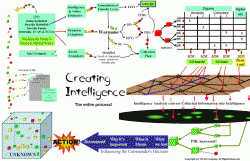
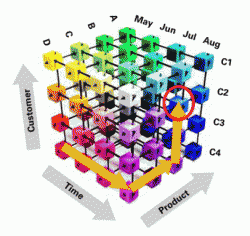
My job and what I do currently is to solve “impossible” problems. Problems other analysts have given up on because there is too much data, too little time, or it’s just too hard. My data sets resemble an OLAP (OnLine Analytic Processing) cube.
An OLAP cube is a visual model of three dimensions of data. I am in essence called on to learn a subject as fast as possible, become close to an expert on it, and then analyze and synthesize a solution to a problem.
Bigger problem sets are usually 90 days…smaller ones four days. Recently an epidemiologist we worked with pointed out that what we did in four days would have taken him at least a year, if not two.
I’ve had to become an expert on everything from nuclear and biological weapons to illicit financial networks. What does sharia compliant mean? I can tell you. What does Shor’s algorithm have to do with quantum entanglement? I can tell you.
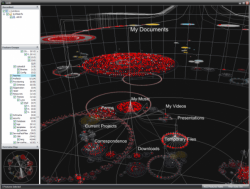
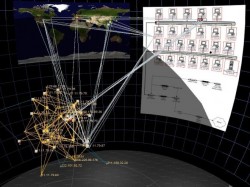
I use tools (the image to the lower left and lower right are images of visual analytics Starlight creates) that are generally acquired as part of a larger budget (one not available to the public). We use semantic mapping and entity extraction, combined with every piece of data we can get our hands on. Our facilities house entire copies of 10 years of military message traffic. We have complete copies of many SECRET and TOP SECRET intelligence databases joined with open source databases like LiveShips.
We stick it all in a virtual sandboxed environment and see what pops up. What data we can’t get up front we use “cut outs” to acquire. We code API’s and then we take existing programs like Palantir and force them work with others like Starlight.
We use Hadoop as a distributing computing system and we use Field Programmable Gate Arrays (FPGA) to take it outside the wire. We use NoSql to avoid inter-relational databases and just create a cloud. We munge data using Google Refine, and then push it through programs like Future Point’s Starlight. When we are done…we take it to operators. Cyber operators…tactical operators…intelligence officers…and we say “Run with it.”
We’ve helped in personnel recovery (the recovery of Captain Scott Speicher for instance) and discovered efforts by the People’s Republic of China (PRC) to acquire tech via illicit means. This is the new intelligence analyst. This intelligence analyst is a data scientist. It’s an empirical look at big data, sifting through it, and finding those same vulnerabilities as in traditional analysis in the enemy and then taking the fight to them.
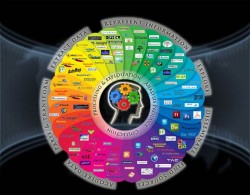
In the figure above are the methodologies I use, and in the figure below are the tools I use.
We try to use as many as possible on any given problem set.
Welcome to spook country.











COMMENTS