I disagree. The deep web was always about the depth of analytics you can derive from social behavior on the internet, document repositories available for extrapolation, and otherwise not “popular” or user-generated specific data. Meaning, one dude writing on a blog post is not deep web. But rather, the behavior of all WordPress users and analytics derived from extrapolated user-generated content.
Think of the “deep web” as the part of the library way down in the basement where cheerleaders meet the football jock for a make-out session but don’t even look at the book titles. It’s where Jack Murphy ran into some feminists who made a video about being naked with a rubber chicken. It’s the part of the library really useful for a specific type of user, but everyone else does not give a chickens..uh..yeah.
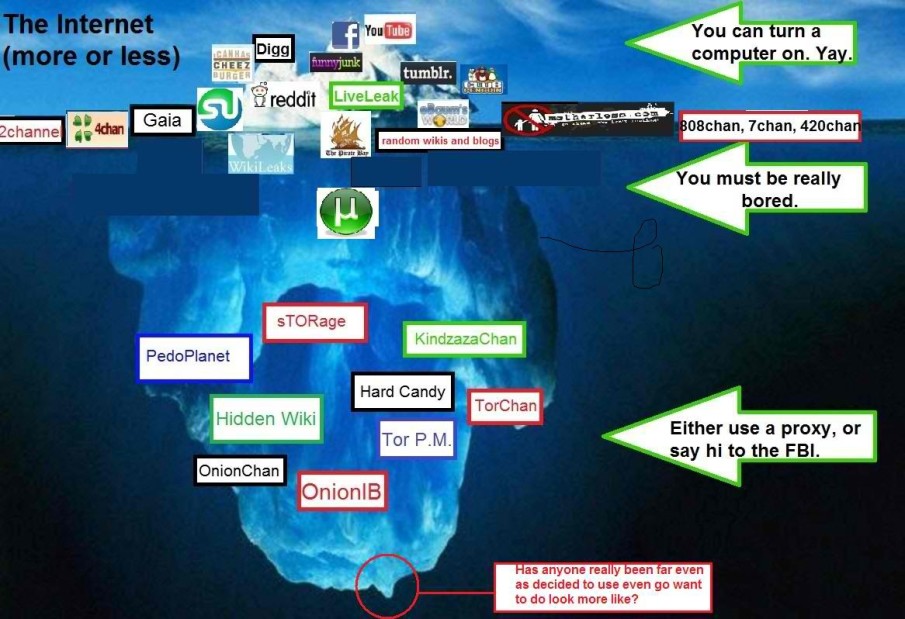
Finally! The “juicy” stuff. According to this article, Cisco invented the term “dark web” to dumb down computer concepts to its customers generate buzz about a product they claimed would help combat this evil presence on the web…waaay back in 2009. Lulz. The dark web is a series of sub-nets (not DNS sub-nets, for all the dorks out there) that are riding on an existing or ad-hoc infrastructure. Meaning they use facets of your ISP-provided infrastructure, or use improvised cellular or wireless signals, to connect. It’s where all the evil on the Internet went after the FBI arrested Kevin Mitnick and held him for seven years on, uh…questionable charges. Arrested for the crime of “social engineering” in 1995? I think not. These guys hadn’t even read the Cuckoo’s Egg yet. Hell, they STILL like to work with manila folders and number two pencils. So one of the most popular interfaces to the “dark web” is Tor, which was an acronym for “The Onion Router.”
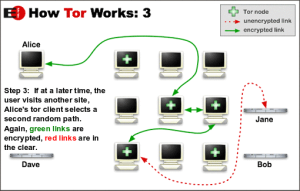
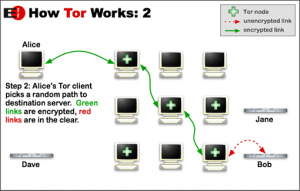
Without getting too complicated, TOR routing takes the basic components of your data and feeds it through various volunteer systems, and then re-assembles it at an “exit pipe.” Tracing it is similar to peeling back layers on an onion. You can run Tor the way I do, through a command line interface, or through a GUI (Generic User Interface) provided by The TOR Network. Tor includes a proxy, called Privoxy, which also needs to be activated to run correctly.
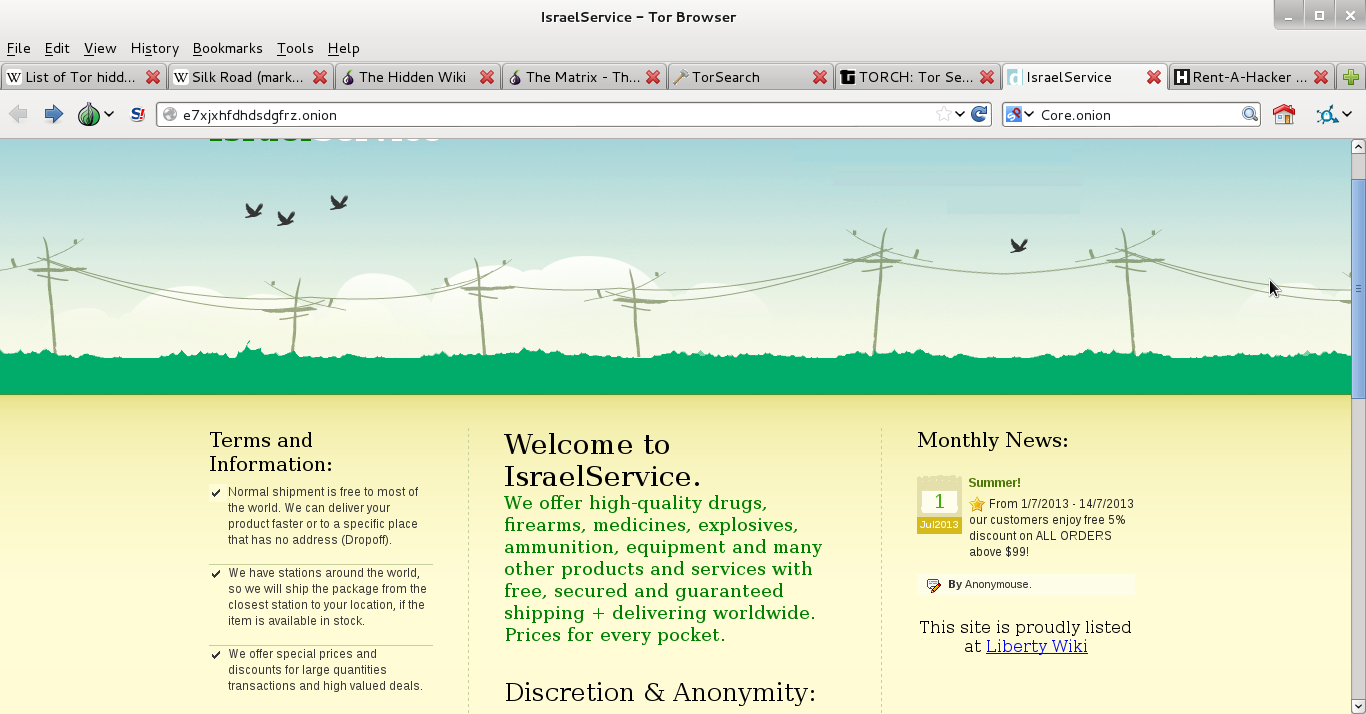
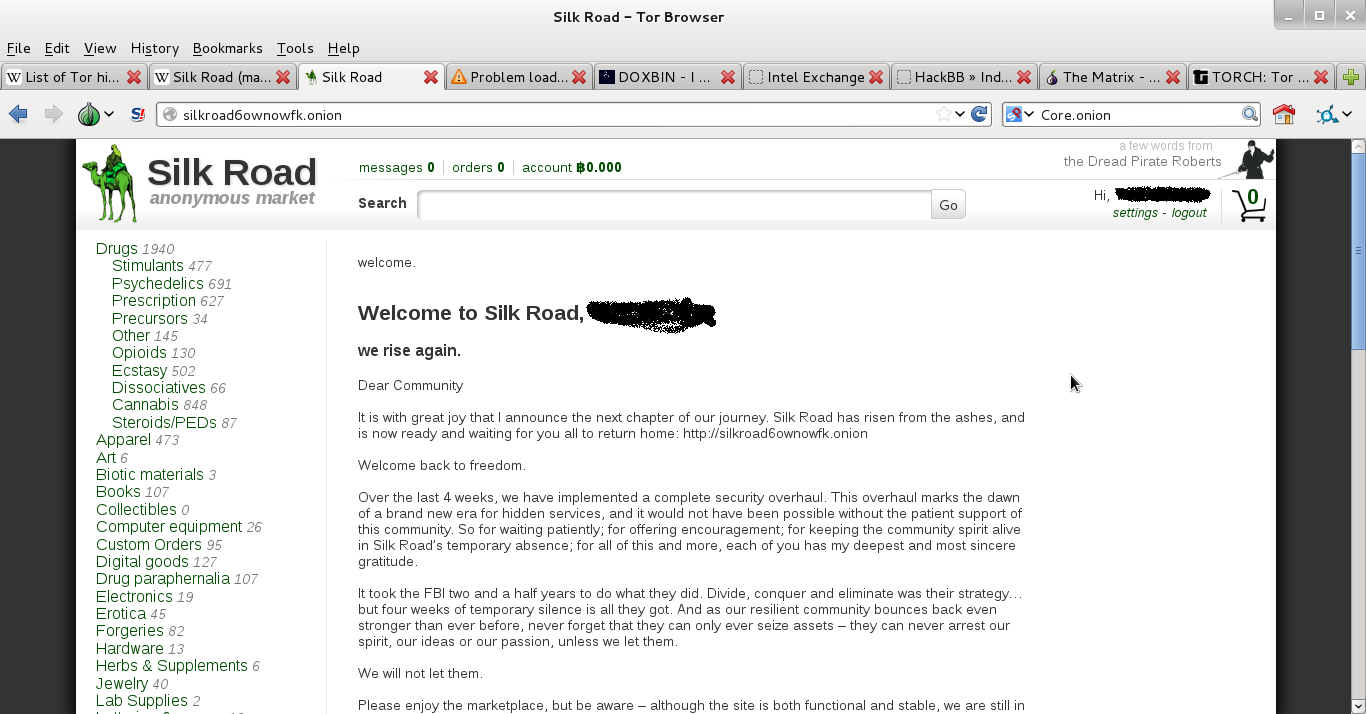
I’m not getting into specifics on HOW to do this because the point of this is for you to understand distinction, not design. The TOR Network is designed in its current incarnation to increase your anonymity online, but was designed back in the day by the Office of Naval Research as a way to bypass censorship and provide spies a means to communicate. So you do get anonymity from most people; whether you get it from the government is questionable. That said, you can find the following on the TOR network: gun runners, drug-dealers, pedophiles, Russian mobsters (or people claiming to be Russian mobsters), assassins, and of course, hackers. So not much different from your internet right?
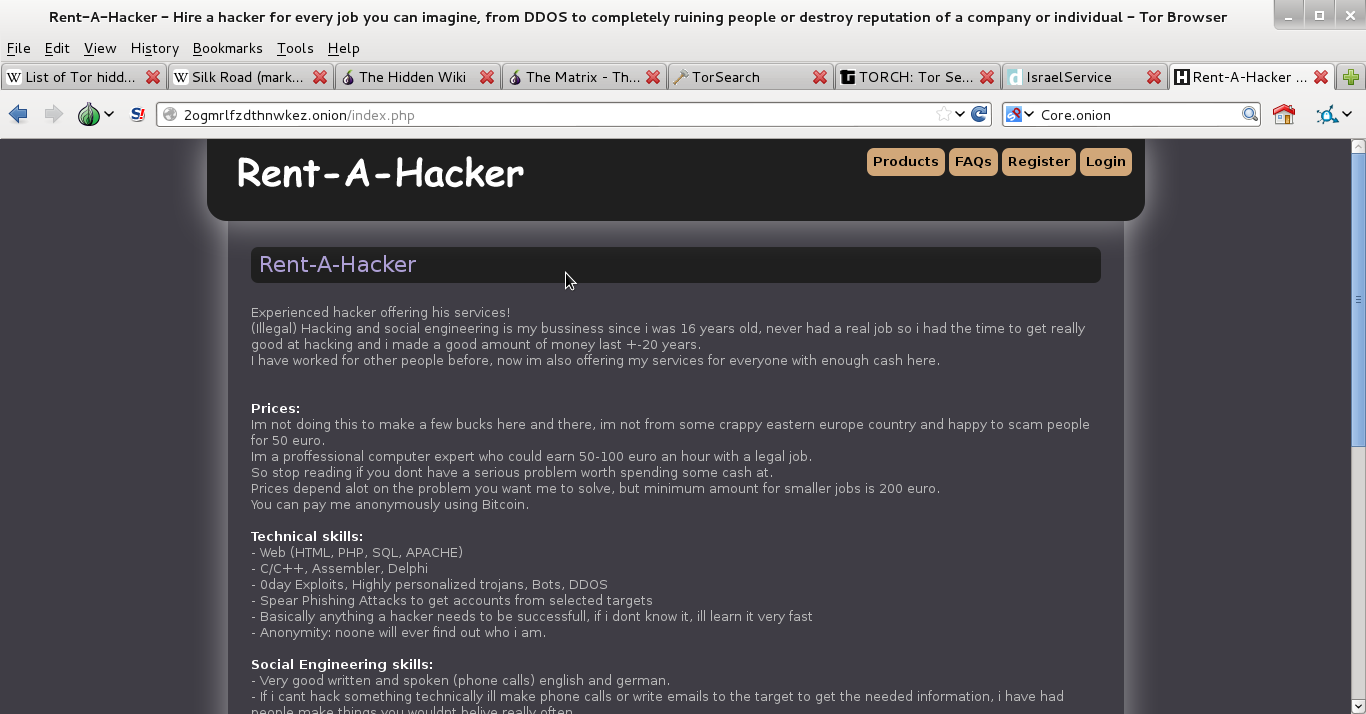
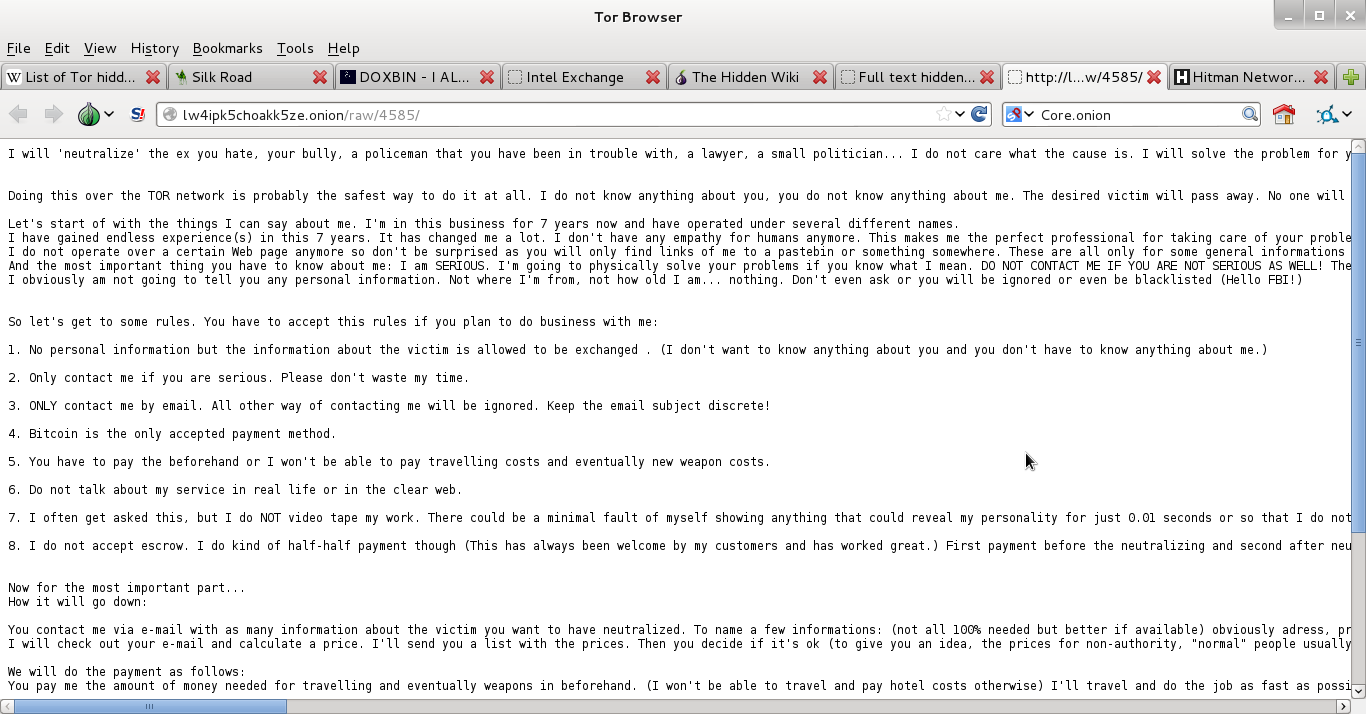
You want to rent a hacker for nefarious purposes? You can find them here. Weapons? Find them here. Drugs? No shortages of that here either. Finally, you can find your very own assassin here as well. That ends tonight’s chapter kiddies. The second part of this will discuss cjdns and sub-nets such as Hyperboria and a few other goodies. See you next week…same Bat-time…same Bat-channel.
Finally, I would not recommend visiting these sites on Tor unless you are confident that you know what you are doing. Anything from packet leaks to lack of a proxy will get your shizzle fucked up.
“Case had always taken it for granted that the real bosses, the kingpins in a given industry, would be both more and less than people… He’d seen it in the men who’d crippled him in Memphis, he’d seen Wage affect the semblance of it in Night City, and it had allowed him to accept Armitrage’s flatness and lack of feeling. He’d always imagined it as a gradual and willing accommodation of the machine, the system, the parent organism. It was the root of street cool, too, the knowing posture that implied connection, invisible lines up to hidden levels of influence.” ― William Gibson, Neuromancer
(Continue reading Government Hackers and the Dark Web Part 2)









COMMENTS