
The slow bleed: How China is ‘managing’ the decline of America and replacing us as a global superpower
In the coming years, China will have reached a point where they are surpassing currently developed military and industrial technology.

In the coming years, China will have reached a point where they are surpassing currently developed military and industrial technology.

In semi-secure anonymous realm of the Net, it can be zero-to-jugular in a second flat, and some folks are looking to shave off those last few tenths of a second from their last year’s olympic qualifying time. The Internet really is a double-edged cyber sword, isn’t it?

The movement of people and goods in this modern, global society is extremely fluid. ISIS has taken advantage of the openness of our western societies as well as the usefulness of the Internet to spread their message and recruit members.

WASHINGTON — Newly released emails show State Department staffers wrestled in December 2010 over a serious technical problem with then-Secretary of State Hillary Clinton’s home email server. They temporarily disabled security features, which left the server more vulnerable to hackers. Weeks later, hackers attacked the server so seriously it was shut down. The emails were […]

Some sites will share your information, including email addresses and user preferences, which can increase spam. To reduce that, consider hiding your email address or changing the settings so that only a few people you trust can see it. Also, check out the site’s referral policy so you don’t unintentionally sign up your friends to get spam.

Any collision between two great powers is something we have worked for over 70 years to avoid, but we’re in a period of dynamic competition, and we’ve got to address tha

Nine months after President Obama and President Xi Jinping of China agreed to a broad crackdown on cyberespionage aimed at curbing the theft of intellectual property, the first detailed study of Chinese hacking has found a sharp drop-off in almost daily raids on Silicon Valley firms, military contractors and other commercial targets. But the study, conducted by the iSight intelligence […]

ISIS has collected information on 77 U.S. and NATO air force facilities around the world and is calling on supporters to attack them, according to South Korea’s intelligence agency. The terror group has also released information on individuals in 21 countries, including the personal details of one employee of a South Korean welfare organization, the […]

Defense Secretary Ash Carter wants to open the door for more “lateral entry” into the military‘s upper ranks, clearing the way for lifelong civilians with vital skills and strong résumés to enter the officer corps as high as the O-6 paygrade. The idea is controversial, to say the very least. For many in the rank-and-file […]

Unfortunately, despite all our progress against [Daesh] on the battlefield and in the financial realm, our efforts have not reduced the group’s terrorism capability and global reach. The resources needed for terrorism are very modest, and the group would have to suffer even heavier losses of territory, manpower, and money for its terrorist capacity to decline significantly.

North Korean hackers reportedly infiltrated a computer network belonging to a South Korean aerospace firm’s computer network and made off with blueprints for the F-15 Eagle—the American-designed jet fighter that forms the backbone of the U.S. and South Korean air forces. But don’t panic quite yet. There’s not much Pyongyang’s engineers can actually do with […]
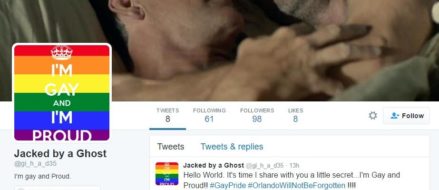
Twitter accounts belonging to supporters of the Islamic State militant group (ISIS) have been hacked in the wake of the Orlando shooting, with jihadist messages replaced with links to gay pornography. A hacker affiliated with the hacktivist collective Anonymous, who uses the online moniker WauchulaGhost, first began hijacking pro-ISIS Twitter accounts several months ago. Following […]