Of note, the amount of publicly available information (PAI) online is absolutely staggering. Cybersecurity is a multi-billion dollar industry for a reason, as is cybercrime! For a reference, we’re talking hundreds of millions of stolen credentials — usernames, emails, and passwords — that are now in the “public” domain and freely accessible to any number of actors.
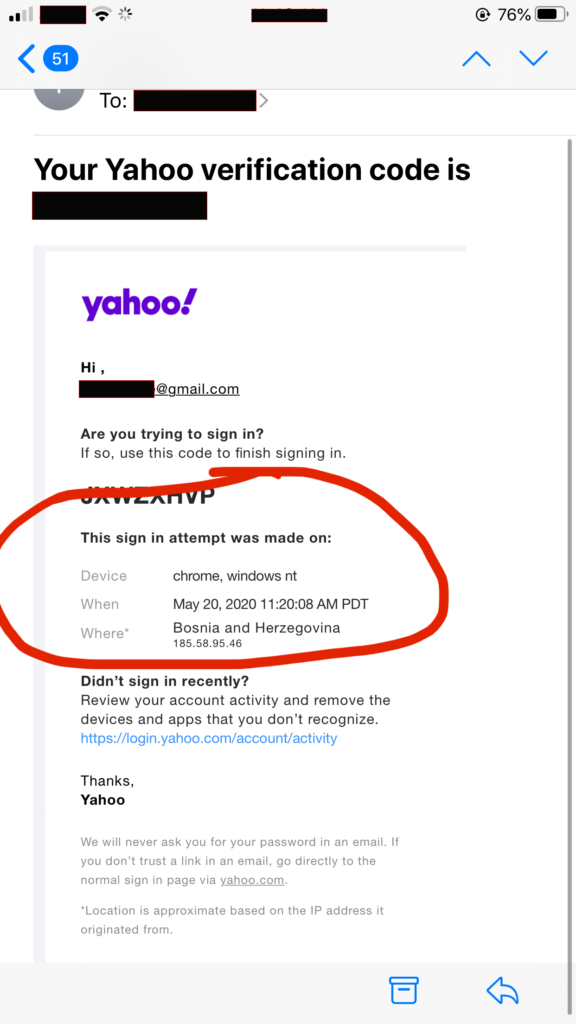
I conducted a basic search of my relative’s back-up email address which yielded the below results. As you can see, their specific email address had been observed in no fewer than 10 separate data breaches over a period of several years. The longer an email has been “in circulation,” the greater the likelihood of a breach occurring, and the greater the vulnerability.

As we can see, my relative’s email account was observed in the above 10 breaches. This means that their credentials are certainly out “in the wild” waiting to be used by a criminal in an attempt to access their account and conduct criminal activity. And this is what we saw above when they attempted to access my relative’s Yahoo account.
Diving into the data
After getting a sense of how compromised my relative’s various accounts were — through no fault of their own, mind you — I jumped into the specific datasets to see if I could locate their unique password based on the email address listed in the Yahoo email.
Sure enough, the password was easily located among several collections of stolen datasets that are also available for the purpose of security research such as this. Two particular sites I find useful are Intelligence X and DeHashed. The below screenshot is an example of the data (username/email and password), in plain text (i.e. not encrypted) for me to see alongside thousands and thousands of others.
Not only does this data provide me with the usernames and password of my relative’s original account, but it also occasionally provides me with new emails and passwords to search for. This would allow me to expand my search if I were conducting extensive security research (similar to our OSINT work here on Princess Basmah).
What to do with the password (travel to Bosnia, of course)
Now that I have my relative’s password, I can attempt to use it. Keep in mind, this is extremely illegal except in the case of conducting an authorized, attorney-approved penetration test — which this isn’t. This is no doubt what the potential hackers attempted when they tried to access my relative’s account using publicly available credentials stolen from the various companies my relative uses.
Had their attempt worked, they would have gained unauthorized access to my relative’s account. This would provide them with an additional attack surface they could use to pivot to another nefarious act, such as taking over a social media account, resetting my relative’s bank password, locking them out of the account, and any other number of things. As we’ve preached before, simply look into a “SIM swap attack” and use that as your creative template for how that could be applied to taking over social media accounts, bank accounts, other emails, and how it could affect other family members, etc.
The key takeaways
So you don’t want this to happen to you? Got it. Few people do. Thankfully, the fix is unbelievably easy. The question of a breach happening and your credentials being stolen is truly not if, but when. Therefore, good digital security hygiene is really all it takes to minimize your vulnerabilities, limit attack surface, and press on with your life of freedom.
The first thing to do to avoid this type of incident is to not use the same password across multiple accounts. Yes, this may seem fairly obvious, but using one password for multiple accounts is far more common that we’d like to admit. The cost of security is convenience. And what’s more inconvenient than having to remember 50 different, unique, complex passwords (all with numbers, characters, and at least one capital letter)? I’ve busted at least two intelligent and capable relatives using the same password to log in across all of their accounts. Thankfully I noticed it before the bad guys got around to trying it first.
Fortunately, there’s a free fix for that: use a password manager. Password managers allow users to store their unique account passwords in one location, thereby removing the need to remember all of your unique account information. Yes, this presents some distinct vulnerabilities in its own right, but it’s far better than giving an attacker access to all of your accounts by recycling the same password. Do some research on your own on password managers and make the call if it’s worth implementing for your own daily digital routine.
We’re going to keep covering topics like this, and look forward to your thoughts on them. We can’t emphasize enough how critical data security is to all of life’s adventures, be they military or intelligence operations, or just everyday life.
Thanks for listening.










COMMENTS