The Chinese education system is one geared toward developing knowledge indigenously, and what it cannot create or produce indigenously, it extracts from abroad. According to William Hannas, the Chinese sought early on to separate foreign (initially Russo-Soviet) culture from the knowledge whence it came. The specific intent of the Chinese is to extract knowledge but not contaminate the Chinese culture with any kind of Western influence.
This is the concept of ti-yong. Ti-yong is “to keep China’s style of learning to maintain societal essence and adopt Western learning for practical use.” (Hannas 2013). Students are encouraged in the STEM areas as opposed to the Western concept of a liberal arts education. Along this track, the best are carefully selected for Torch programs or universities. Torch programs are regionally controlled industrial and academic R&D fusion city centers. There are at least 50 of these centers dedicated toward integrating academic R&D into a applied business process for either military or commercial development. This is similar to our Federally Funded Research and Development Centers (FFRDCs). Other students are selected for university positions as interns under prestigious academics.
The PRC likes to use this student population as spies. They get sent abroad to universities around the world, either wittingly or unwittingly, to study in areas that the Commission for Science, Technology and Industry for National Defense (COSTIND) deems weak within the Chinese strategy. This commission is today known under the benignly disingenuous term Ministry of Science and Technology (MOST). The intent of MOST is to use these students in an unwitting or witting capacity to acquire knowledge, processes, or technology that the PRC does not yet have.
To support this effort and part of the overall effort of qingbao (a term which is nearly synonymous to both intelligence and information), the PRC has a massive library system. Based on the PRC’s own estimates from the Institute of Scientific and Technical Information of China (ISTIC), here are the following holdings as of 2005: 1.2 million foreign conference papers, 1.8 million foreign S&T reports, 270,000 foreign periodicals, 9.8 million microfilmed products, 330,00 audio visual products, 4.722 billion titles and abstracts in databases, 644 million full text documents in databases. These holdings are spread over 353 computer networked institutes. These institutes are overseen by intelligence experts and have an average user base of 27 million as of 2005. Chinese who accessed overseas networks through the institutes to obtain foreign S&T materials numbered slightly over one million. (Hannas 2013). This means that the Chinese are using academic virtual credentials to obtain records from other countries that supply the data on the condition that you are an academic. This system is not the same as their intelligence networks or their Internet.
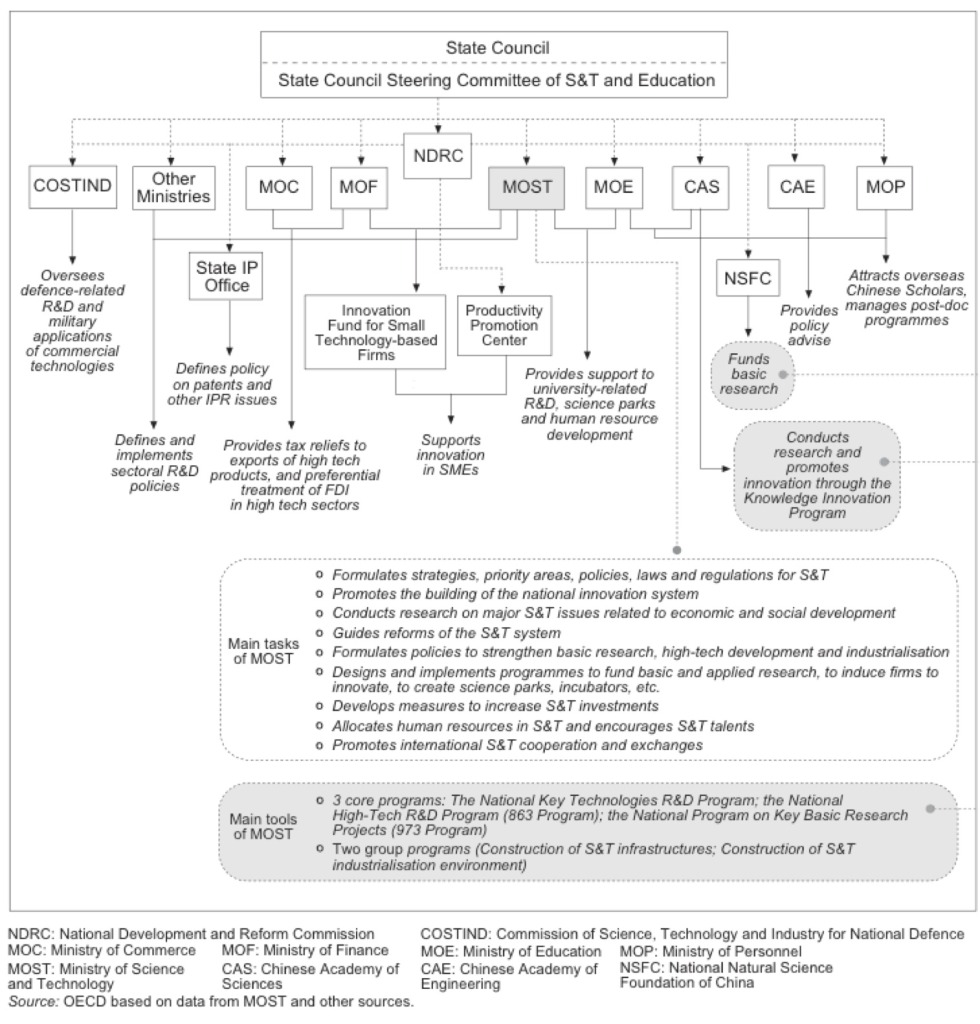
This system is not available to you in any way, shape, or form. This is not Google. This is not an American public library system. This is as if all the library systems in the US fell under the control of the Office of the Director of National Intelligence (ODNI). It is qingbao. This is not your paramilitary grand-dad’s intelligence.
Before you ask, “But tinfoil hat dude, is it ALL intentional?” Yes. Yes it is. The most brilliant part of Harmonious Fist is that the PRC tells you all about it in their five and 20 year plans.
How do you think I found it? The PRC relies on the Western attributes of apathy and ADHD. So to read these hundred page documents you’ll need a couple of things. You’ll need to be able to optical character recognition (OCR) tons of crappy digitized documents; you’ll need to translate them from either Mandarin or Cantonese; and then, you’ll need to conduct natural language extraction and processing (NLEP/NLP). If you don’t know what lemmatisation is, you’ll probably need a Chinese linguist and about ten years of time.
“Is that all there is to Harmonious Fist,” you ask. “Where does this “het-net” shit come in,” you ask. “What the hell happened to Team XeYe,” you ask. No. This is not all. This is just the educational system directed at undermining Western dominance of the globe. Next we will focus on the economic and technological facets of this system that fall under the same strategy. This is my discovery process that led me from a project about a tiger team of hackers to mapping the entire espionage complex of the PRC and identifying where the Chinese plan on going from there.
Please enjoy the common military custom of “hurry up and wait”…for part two.
I am the Architect. I created the Matrix. I’ve been waiting for you. You have many questions, and although the process has altered your consciousness, you remain irrevocably human. Ergo, some of my answers you will understand, and some of them you will not. Concordantly, while your first question may be the most pertinent, you may or may not realize it is also the most irrelevant. -The Architect, The Matrix Reloaded
—–
Lam, Willy Wo-Lap, and Jamestown Foundation (Washington, D.C.). Changing of the Guard: Beijing Grooms Sixth-Generation Cadres for 2020s. Washington, DC: Jamestown Foundation, 2010.
William , Hannas, Mulvenon James, and Puglisi Anna. Chinese Industrial Espionage: Technology Acquisition and Military Modernization. Asian Security Studies. Routledge, 2013.










COMMENTS