Much has been made about Operational Security (OPSEC) in recent years, much of it revolving around high level politicians or even congressional staffers leaking information about sensitive military operations such as the SEAL Team Six raid in Pakistan that killed Bin Laden. While it is true that Pentagon staffers and politicians leak information to the press (a lot of is intentionally or unintentionally false) the military would be better served by taking a look into the mirror when it comes to preserving operational security.
The following is DOD’s definition of what OPSEC is:
E2.1.3. Operations Security (OPSEC). A process of identifying critical information and analyzing friendly actions attendant to military operations and other activities including:
E2.1.3.1. Identify those actions that can be observed by adversary intelligence systems.
E2.1.3.2. Determining indicators that hostile intelligence systems might obtain that could be interpreted or pieced together to derive critical intelligence in time to be useful to adversaries.
E2.1.3.3. Selecting and executing measures that eliminate or reduce to an acceptable level the vulnerabilities of friendly actions to adversary exploitation.
For a more in-depth explanation, SOFREP published an article about what OPSEC is and is not, which can be found here. The bottom line is that America can no long run covert and clandestine operations the way we used to. Having recently written about Detachment A in Berlin, it becomes clear that the military could never run a clandestine unit like it in this day and age. In the past, I’ve had some at times heated conversations with the old guard but the reality is what it is, the operational environment has changed.
I remember a few years ago there was an incident where a couple of Americans were detained crossing the border from Tunisia into Libya. The Libyan border guards photographed their passports and ID cards which ended up on the internet. I googled their names and to my unsurprise, one of them ran 10K races in Fayetteville, North Carolina the home of 3rd Special Forces Group and Delta Force. The proliferation of communications technology has changed everything.
Take a more recent example, the SEAL Team Six raid in Yemen in which one SEAL was killed and one Osprey aircraft was lost. This was not a clandestine operation and the actor (America) behind the raid was never intended to be disguised, so in this case there was no OPSEC violation but I post this here to remind people how easy it is to be compromised.
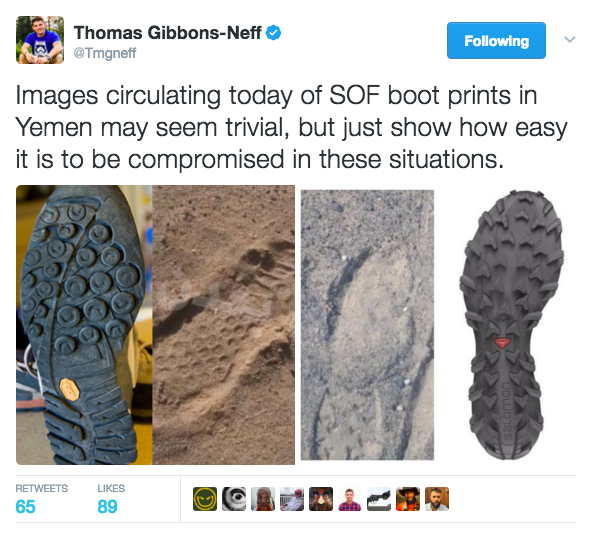
In 2017, our soldiers carry out their tasks in an operational environment in which every third world dirt farmer has a cellular phone in his pocket. That phone probably has a camera on it. That same phone may very well have internet access. That dirt farmer will probably take a picture of any odd sightings of Americans trying to be sneaky, and will almost certainly share it with friends if not post it on the internet. Case in point:
Already have an account? Sign In
Two ways to continue to read this article.
Subscribe
$1.99
every 4 weeks
- Unlimited access to all articles
- Support independent journalism
- Ad-free reading experience
Subscribe Now
Recurring Monthly. Cancel Anytime.

This was a team of Special Operations soldiers sent on a low-visibility mission to Libya. Their photograph was taken by curious Libyans on the airbase the moment they arrived, and of course that picture was soon all over Facebook. This is the new reality of our operational environment. The pictures made other militias in the area aware of the American military presence and the team had to be extracted just as quickly as they had arrived. Some big outlets in the mainstream media picked up the story but when I published it months later there was a wave of outraged OPSEC warriors who don’t understand OPSEC or OSINT (open source intelligence).
I encountered the same anger from the community when writing about the CIA’s Timber Sycamore program in Syria. When asked, it turned out that they were completely unaware of the fact that this covert CIA program has a fairly detailed wikipedia entry.
The OPSEC of many aviation assets utilized by the Special Operations community have also been compromised. We’ll publish a more in-depth look at that topic but suffice to say it is easy to connect the dots using websites like flightradar24 and correlating the information with private contractors who lease their aircraft for SOF support.
These are just the OPSEC violations that we know about. Other technologies have the potential to make life even more difficult for our Special Operations troops. Did you know that an adversary could take a picture of you holding the keys to your bed-down site and then use computer software to computer the dimensions of those keys and have an automated key maker churn out a copy for himself?
Did you know that the technology exists to photograph your fingerprints on a glass from across the room? Those photographs can than be used to produce copies of your fingerprints, those copies could be turned into gel pads worn over an adversary’s fingers. Bio-metrically, the bad guy becomes to the good guy.
This is not to say that running covert or clandestine operations is impossible, at least not yet. However, the protocols, tactics, techniques, and procedures currently used to maintain OPSEC simply do not work. Kids on instagram are cracking the code to Delta Force’s callsign patch alphanumeric system. Bad guys and red teamers alike are fleshing out the entire task organization of your Special Operations Task Force.
Time to re-think our approach to OPSEC once and for all rather than whining about it on social media with some expectation that America is going to return to the classic 1950’s era covert operations. The past is the past, and none of us can have it back.
Featured image courtesy of Stratcom.mil












COMMENTS