Given that structural stealth is not effective, what can we do to protect our pilots and carry out the mission?
Anti-radar countermeasures like chaff and flares have been in use from the time radar was introduced. Chaff, carried in a dispenser, is a cloud of silver foil scattered behind the aircraft. When released, radar waves reflect off the strips. The effect is to confuse enemy radar. Flares burn bright and hot. Aircraft release them to confuse infrared seekers.
The way to defeat radar in the new battlespace increasingly relies on electronic countermeasures (ECM). People talk about electronic countermeasures, electronic counter-countermeasures, and electronic support measures. It gets confusing. Mark Hewer and Leonardo defense and aerospace have reduced it to a single term: Digital Stealth. Digital stealth encompasses all the technology used to dominate the electromagnetic spectrum and defeat radars that are trying to kill our aircraft.
Digital Stealth – What do we want to achieve?
Let’s look at how radars kill an aircraft. We talked about it in The Anti-Stealth Kill Chain but we will go into it in more detail. In their simplest form, air defense systems consist of an acquisition radar, a targeting radar, and a weapons system.
The acquisition radar detects the airborne threat. Most Western acquisition radars operate in the X and S bands and can be defeated by structural stealth. Russian acquisition radars operate in the VHF band and cannot be defeated by structural stealth. A Western installation will typically have two radars, and a Russian installation three or more, including two acquisition radars operating in different bands. The acquisition radar passes the stealth contact to the targeting radar as part of the kill chain.
Targeting radars tend to operate in the S and X bands. They track the target as it approaches and guide weapons to destroy it.
Now. How does targeting radar do its job? The simplest approach is to lock the target and direct a missile to it. The radar fixes on the aircraft. A missile is fired. The targeting radar is data-linked to the missile. You can draw a straight line from the radar to the target. If the missile deviates from that line, the radar directs the missile’s servos to move its control surfaces and swing the missile back onto the line. Course corrections are made until the missile destroys the target.
There are two ways for digital stealth to disrupt that kill chain.
- Jamming – if we confuse the enemy radars, we prevent them from locking our aircraft. They may never fire their missiles.
- Decoys – if we can make the targeting radar look elsewhere, the enemy will fire their missile in the wrong direction
Digital Stealth in the Attack – Jamming
Let’s say you have agreed to meet a friend at the train station. You step onto the platform as the train rolls to a stop. The carriage doors slide open, and – five hundred people step out. You can’t find your friend because she’s buried in the mob. That’s jamming. When we’re approaching the target and we spot enemy radar, we broadcast a lot of electromagnetic noise on the enemy wavelength. They won’t see our aircraft because it is buried in the clutter. Figure 3 shows how jamming obscures our aircraft.
There are two issues with jamming. First, the moment you start jamming, the enemy knows you are there, and they look harder. On the other hand, once you concede that structural stealth is defeated by long-wave radar, you might decide you have nothing to lose.
The way to defeat this kind of jamming is to frequency-hop. The attacker is jamming one frequency, so the defender switches to another. The two systems hop around, the attacker chasing the defender.
There is only one way to defeat the frequency-agile defense. That is to jam the entire range of frequencies used by the enemy radar. If the enemy radar is operating in the X band, you throw out noise over all frequencies from 8 GHz to 12 GHz. Such full-spectrum jamming requires enormous amounts of power. Now, the most modern Russian electronic warfare systems are powerful. The Murmansk-BN system, deployed to Iran, can be effective to 5,000 miles. That’s a lot of power.
Jamming systems can be carried on either the attacking aircraft or on a support aircraft. Figure 4 is Marconi’s Skyshadow jamming pod, designed in the 1970s and still in use.

The Skyshadow is capable of the brute-force jamming described above, but it is also capable of more subtle electronic warfare. Rather than obscuring the enemy’s radar with noise, it is possible to create “ghost” targets to make the enemy look somewhere else.
Creating “ghost targets” is complicated. The reader should review the SOFREP article Electronic Warfare 101. In it, we explain that radar pulses are encoded with metadata that allows the radar to compute a target’s speed, direction, and altitude.
Let’s say you want to “spoof” enemy radar by creating a “ghost” aircraft two miles east. You detect the enemy radar and note its profile. Then, you determine the relative bearing of the “ghost” to the enemy radar and encode the ghost metadata to make the spoofed signals indistinguishable from the enemy’s.
We can’t redesign the F-35’s shape as enemy radars get better at finding it. We can digitally fool the enemy into thinking the plane is somewhere else.
American aircraft have been using the AN/ALQ-99 jamming pod. It is instructive to study its specifications. The 99 is capable of jamming frequencies from 60 MHz to 20 GHz. This range extends from the upper end of the VHF to the S, X, and Ku bands. This means the 99 is capable of jamming Russian long-wave radars operating in the higher VHF bands, provided it has sufficient power. Russian radars operating in the lower end of VHF will be immune.
Note that the AN/ALQ-99 is not one jamming pod, but two. It needs to have two to cover the full 60 MHz to 20 GHz jamming spectrum.
The Nebo-M radar operates in the VHF, L and X bands. Should the Nebo-M encounter American attackers jamming in the high VHF, it will downshift to the lower VHF below the 60 MHz floor of the 99. The US has had issues with the AN/ALQ-99 on its EA-18G Growlers for unrelated reasons and will want to address these in its Next Generation Jamming Pod.

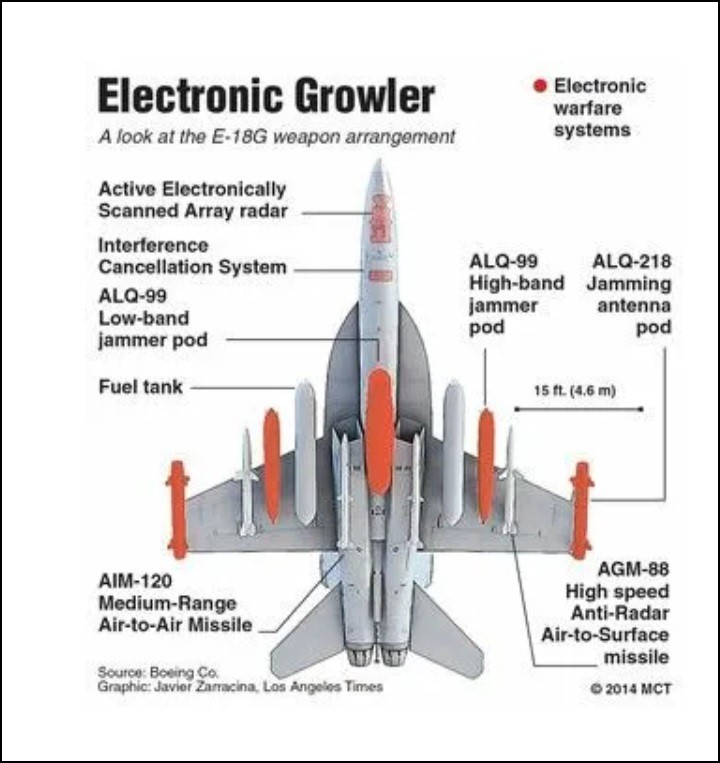
Figure 5 shows the Growler equipped with three AN/ALQ-99 jamming pods, center line, and outboard, to cover its capability spectrum. Notice that the 99s have their own propellers that spin to provide power.
Figure 6 shows the configuration of the Growler’s loadout, including the positions of the jamming pods.
Digital Stealth in the Defense – Decoys
We touched on decoys in previous sections. Chaff dispensers are regularly loaded with disposable digital decoys. We talked about the creation of “ghost” targets. Attack aircraft can deploy electronic decoys, and these have the potential to be far more effective than structural stealth.
There are two ways to deploy digital decoys – onboard and disposable. Attack aircraft frequently adopt both methods.
Onboard towed decoy
An onboard towed decoy is just that. It is a device stowed either in a wingtip pod or in the fuselage. It is deployed in flight, tethered to the aircraft. The decoy sends out signals to threat emitters to make it look like the attacking aircraft is somewhere else.

When the aircraft returns from the mission, the tether is cut, and the decoy is dropped onto a convenient field. Often, they are difficult to find. Hapless farmers have been known to call bomb disposal squads. The decoys are recovered, refurbished, and reused.
Disposable decoys
A disposable decoy is dropped from an aircraft’s chaff dispenser.
The SOFREP article, F-35 Stealth Defeated by Unknown Russian/Iranian Radar, described the electronic warning devices on an attack aircraft. Specifically, the Radar Warning Receiver (RWR) and Electronic Support Measure System (ESMS) pick up radar signals from enemy emitters. These signals are matched to profiles or “signatures” in a threat database and displayed to the pilot.
Those profiles in the threat database are programmed into digital stealth devices to create decoys. We described how a jamming pod creates a “ghost” target. Towed and disposable decoys do the same thing.

Disposable decoys are dropped when a threat is detected. Figures 1 and 8 show Leonardo’s BriteCloud “expendable” decoy. The pilot drops the decoy and takes evasive action. The decoy creates a “ghost” target, more attractive to the enemy than the attacking aircraft. An air defense missile is fired, guided by the targeting radar, and the decoy draws it away.
Digital Stealth – The Database is Key
Building the threat database is critical to digital stealth. In Electronic Warfare 101, we described how Iran used a massive missile and drone attack to force Israel to light up its air defense network. This provided Russia and Iran with an opportunity to map it. They recorded all the metadata from Israeli radars and geolocated the devices with sophisticated digital tools. Example: if three Russian aircraft over Syria each detected a radar signal from Israel, they would triangulate it.
The Russians and Iranians then labeled the emitters. Scanning emitters or targeting emitters? What band? THAAD, Golden Dome, or David’s Sling? If there is no match for a particular profile in their database, they label it “Unknown 3572” or whatever until they can identify it positively on later flights. But if they don’t identify it, the unknown can remain a troublesome threat.
This is key: you have to program your jamming pods and decoys with the threats you expect to face on your mission.
On the night of October 25/26, the Israelis encountered an “unknown air defense system.” They thought they had all the Russian and Iranian radars cataloged in their threat database, but they didn’t have that one.
An analyst back at mission control looks at the metadata and compares it to similar threats in the database. “It’s like an S-400… I think.” If the digital stealth system is sophisticated enough (and some are), the revision to the database can be uploaded in real-time. Remember, it still has to be uploaded to the decoys for them to work. This writer does not know if the Israeli system is that sophisticated. Others on the market are. The technology is constantly evolving.
On October 25/26, the unknown remained unknown. The Israelis are casualty-averse, so they went home.
Conclusion: Digital Stealth is the Future
This article has shown that structural stealth, while good, is hitting its limits. Digital stealth is the future. It provides the opportunity to adapt to a rapidly changing threat environment in real-time. Winners in the future battlespace will focus their efforts on digital stealth.
About the Author

You may reach Cameron at: [email protected]
Cameron Curtis has spent thirty years in the financial markets as a trader and risk manager. He was on the trade floor when Saddam’s tanks rolled into Kuwait, when the air wars opened over Baghdad and Belgrade, and when the financial crisis swallowed the world. He’s studied military affairs and warfare all his adult life. His popular Breed series of military adventure thrillers are admired for combining deep expertise with propulsive action. The premises are realistic, the stories adrenaline-fuelled and emotionally engaging.
Check out the books here: Cameron Curtis’s Amazon Page
**Editor’s Note: Looking for the perfect holiday surprise? The BREED series delivers action-packed thrills! -GDM












COMMENTS