To understand why its clear that these guys weren’t just information security professionals, you have to understand the national information system architecture of the PRC. I’m going to describe an analogy for what this looks like. China accesses information across the globe much as we do. They access it via satellite or a series of undersea pipes. However, once data hits the Chinese network topology it is essentially a siege wall. This wall is a composite: the outside wall (or what we call front-facing) and the inside wall (or what we call back facing).
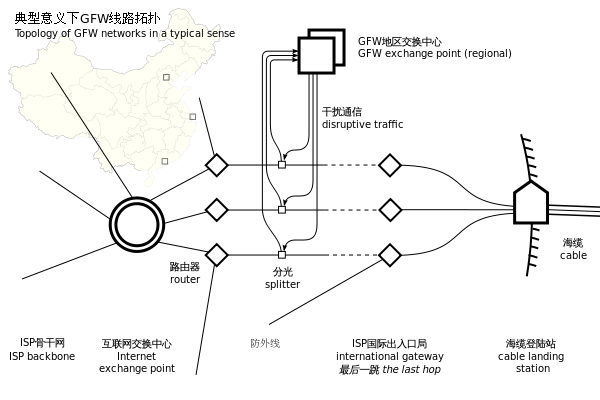
Information entering the PRC’s topology is accepted into the first wall and filtered via a series of networked data diodes that stream packets to firmware and software that evaluate the packets in a kind of “dirty word” search system compromised of many algorithms. The ones that make it are then transferred to the second wall (the back facing wall) were the content is evaluated further largely by content scrapers, and then approved by humans under the guise of Chinese “morality.” Domestic traffic only leaves China under approval by…you guessed it…CN-CERT centers. This a short and incomplete summary of the Golden Shield Project.
The line fed to the global public is that this ensures the safety of users who access .cn sites. Except, when you turn this on its head, it means that they censor what information may or may not leave China. There are many organizations in China that are CN-CERT approved. Topsec and Venustech, for instance. However, ultimately, that approval comes from a series of authorities that stem from the Communist Party and MOST. Remember MOST? So, to tie this little bit together, if you work for CompanyX, the white propaganda you provide your clientèle is that you function as a representative of a security company and assist in building network infrastructure to enhance asset security. That is a real function.
However, the second part of your real function is to assess and undermine the vulnerabilities of the network architecture you are building, and catalog the vulnerabilities and exploit those vulnerabilities for valuable data. Lets put two and two together here. If you are US Company B and you have been hacked and your information security team advises you that the attack originated in China, how is it possible a group of common PRC citizens accomplished this? If the PRC have this Golden Shield, how did these citizens magically make it through, when even dissidents can’t communicate with the US? The answer is: They didn’t. You were attacked by an entity that is sanctioned to do this. It doesn’t matter that the entity ends in .com. The PRC is a command economy. There is no real .com.

Once I was able to reconstruct the efforts by XeYe Team and their actual pattern of life online, and demonstrably show a relationship by the team to the PLA, the people who initially pitched this curve ball at me perked up. They were fairly convinced that I had collected enough derog on CompanyX so their next questions were really to my bosses (yes, apparently I have many). To paraphrase, they said “this is really awesome and it was just kind of a test to see what we would get.” Kinda like, “that’s cool an all…” Their next question was: “Can you do this for everything? Can you show the whole espionage process?” I shook my head vigorously from side to side. My bosses shook their head vigorously from north to south. Pretty easy to figure out who won that argument.
Almost two years later, a heretofore unknown contractor makes off with the results of this work in a brief-of-a-brief-of-a-brief format (don’t get me started, I already earned my Powerpoint tab) and delivers it first to the Chinese, and then to a pretty terrible journalist, catapulting them both to stardom.
It’s a little bit harder to get into Project 973 sites now. They aren’t quite published so openly. You need to login and supply a password. Some archives are missing. Certain doctrinal documents on five and 20 year plans are no longer published so openly. That’s cool, though. He’s a hero for exposing all that evil NSA stuff that the NSA never broke the law to do. Never mind that the bull in the china shop was quietly giggling in the corner at this exciting turn of events.
So there you have it. XeYe Team is really CompanyX and works both sides of the proverbial coin. So we are left with, “What about all those damn het-net references, Coriolanus?” Well, see…that’s where the future lies, and its the final part of all this and ties it into a nice big bow. So you’ll have to wait for the next part of this. Same bat-time, same bat-channel.
*****
As I was saying, she stumbled upon a solution whereby nearly ninety-nine percent of the test subjects accepted the program provided they were given a choice – even if they were only aware of it at a near-unconscious level. While this solution worked, it was fundamentally flawed, creating the otherwise contradictory systemic anomaly, that, if left unchecked, might threaten the system itself. Ergo, those who refused the program, while a minority, would constitute an escalating probability of disaster. -The Architect, Matrix Reloaded
(Featured Image Courtesy: VOANews)











COMMENTS