However, these figures lack substantiation, as credible sources have provided no verification.
Surveillance Activities Revealed
The breach also unearthed the Defense Ministry’s surveillance activities, revealing that the Department of Information and Mass Communications meticulously monitors both Western and Russian media.
This monitoring involves assigning labels such as “positive” (green), “negative” (red), or “neutral” (yellow) to media coverage, followed by detailed reports dispatched to Konashenkov.
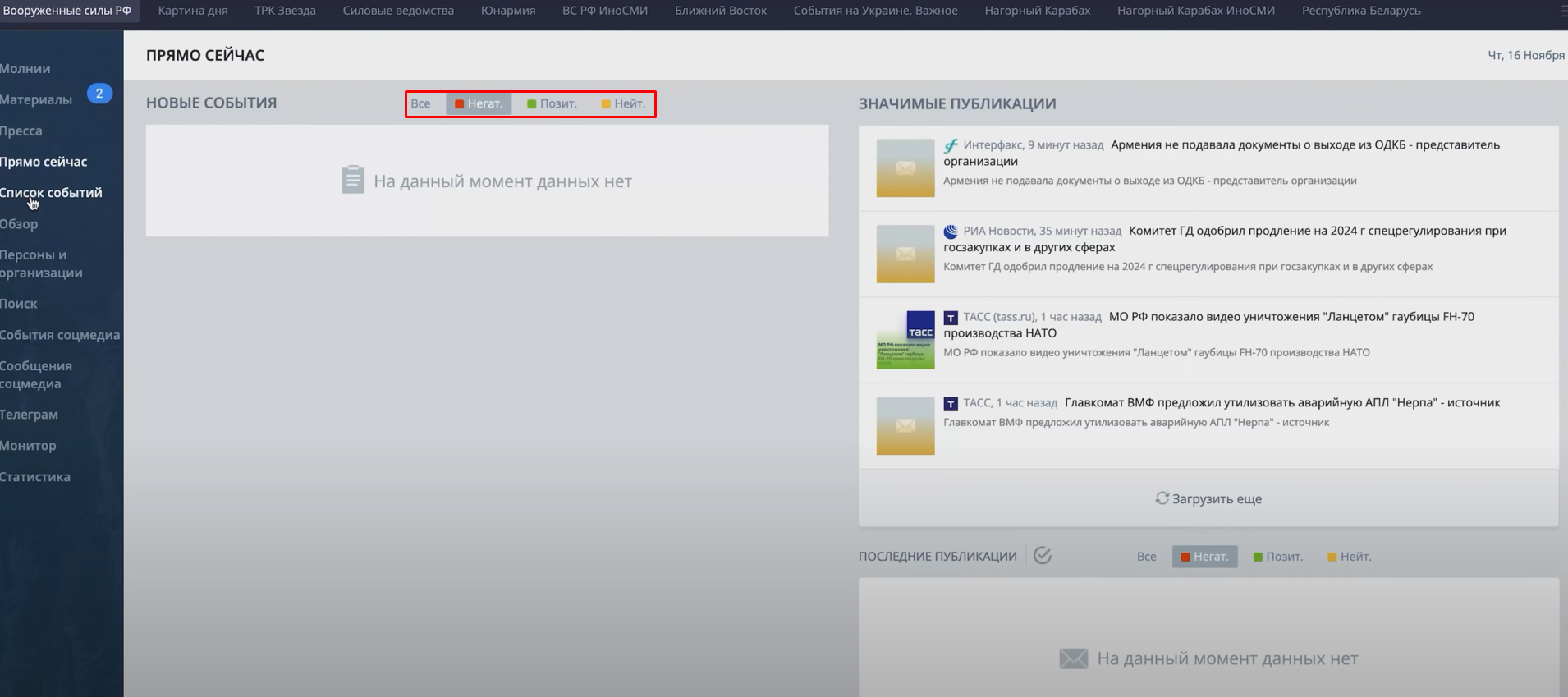
Contrary to the capabilities declared by the system’s developer, the breach unearthed a sophisticated interface that organized events and messages by specific categories.
For instance, it segregates content relating to Zvezda, the Russian Army’s media company, and foreign media coverage of the Russian military, showcasing a detailed analysis far beyond the surface-level monitoring initially advertised.
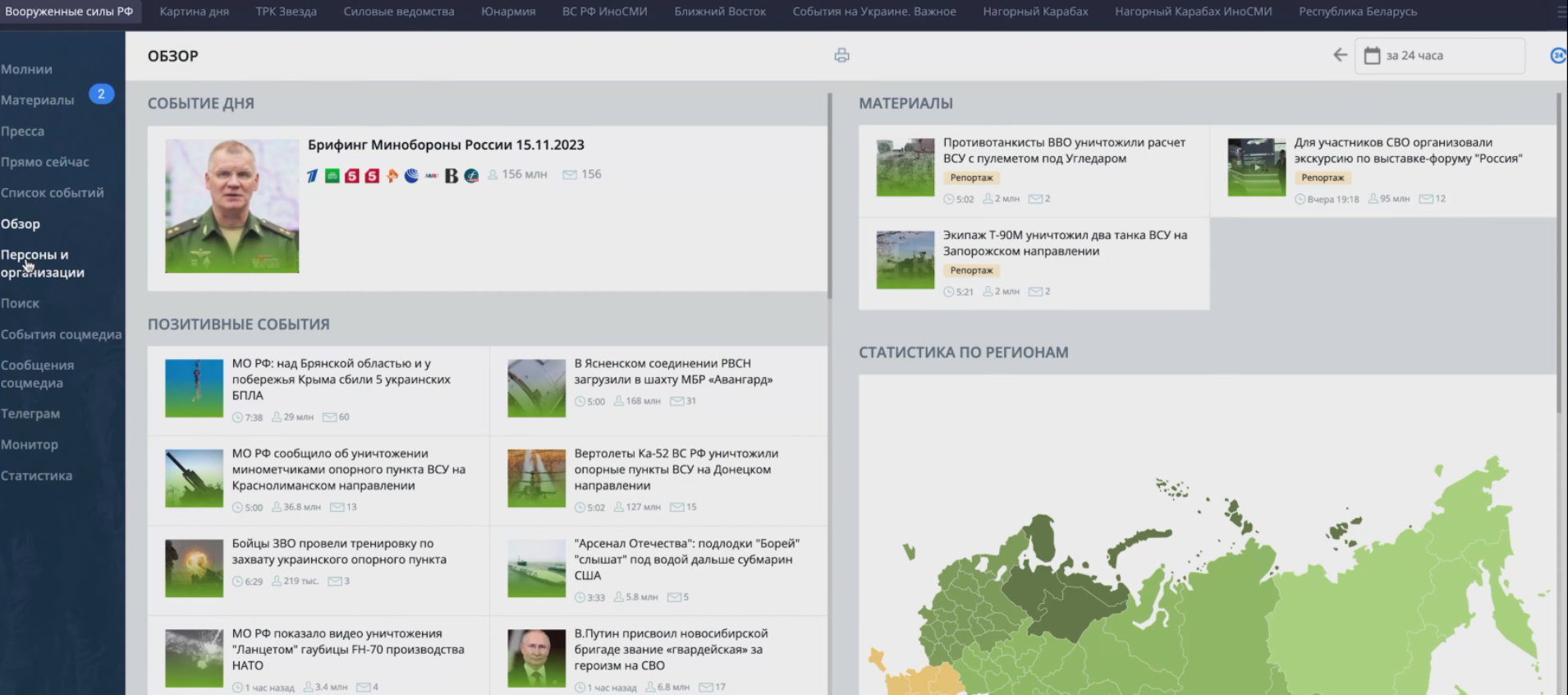
While the system purportedly uploads weekly and monthly reports, its daily addition of prominent Russian print media circulations contributes to an extensive database.
Furthermore, the system pays particular attention to social media, including Telegram, VK, OK, LiveJournal, and others, extracting real-time posts.
Even platforms like Facebook, Instagram, and YouTube are monitored, albeit to a lesser extent. Notably, Ukrainian channels have been identified within the Russian system.
An intriguing feature lies in the system’s tab that analyzes popular Russian Telegram channels, segregating them into positive and negative categories—although access to the list of targeted channels was reportedly unsuccessful.
However, closer scrutiny reveals the system’s underlying agenda – to portray a biased narrative favoring positive representations while systematically disregarding or neutralizing negative reports, especially those critical of the Russian army or political leadership.
A Tool for Manipulating Information
The system predominantly revolves around analyzing the Russian information space. While Western and Ukrainian media are included in the database, their impact on shaping the overall narrative remains minimal.
The skewed analysis significantly relies on Russian sources, subject to censorship and self-censorship, presenting a distorted reflection of reality.
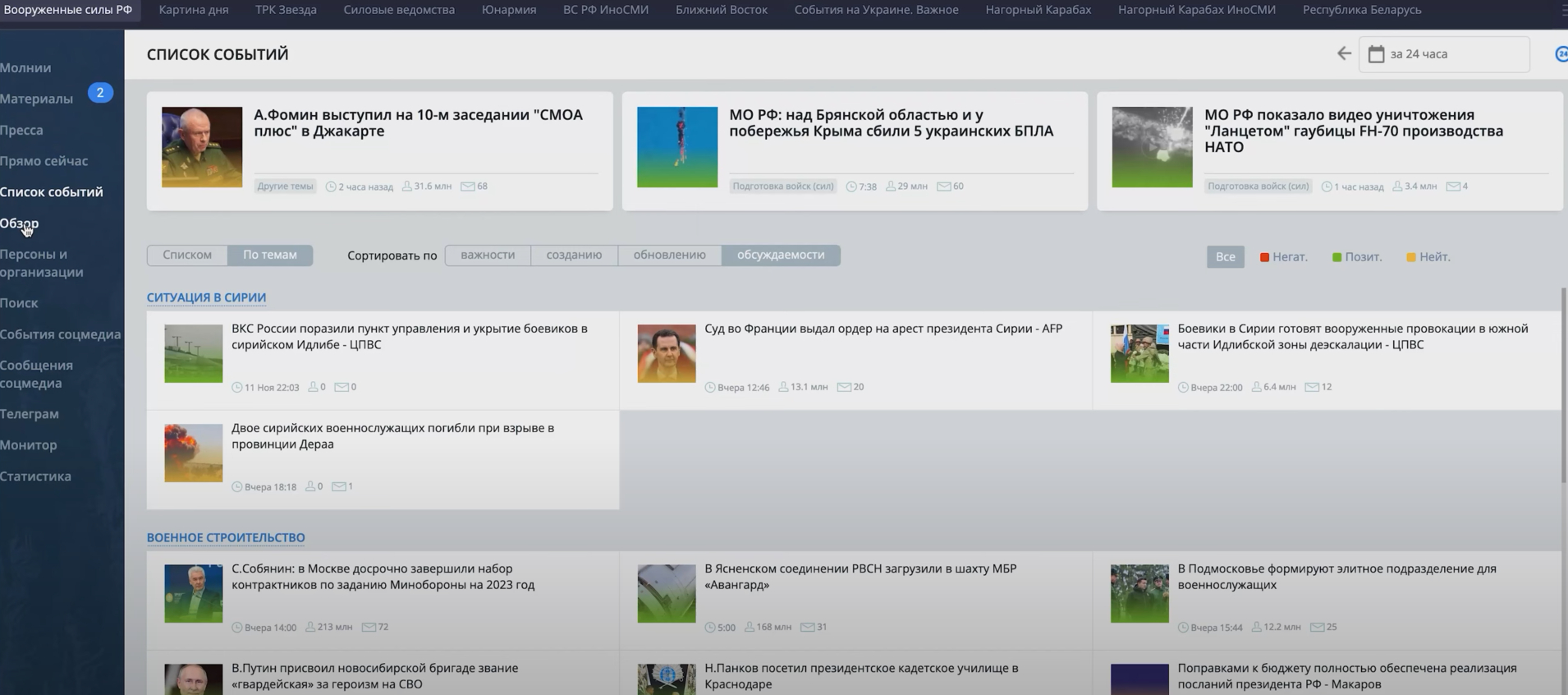
Moreover, the system functions as a tool for manipulation, strategically amplifying positive reports while downplaying or discrediting negative narratives.
For every negative report, the system employs an orchestrated deluge of positive content from the extensive Russian propaganda network, effectively diverting attention and altering perceptions.
The recent example of the successful Ukrainian strike on the Russian Black Sea Fleet‘s headquarters on September 22 illustrates the system’s rapid adaptability in reshaping events, ultimately distorting their true meaning to fit a preconceived narrative.
Thus, the breach reveals that Katyusha operates not merely as a surveillance tool but as a sophisticated mechanism to orchestrate and manipulate information, painting a picture tailored to project a parallel reality crafted by controlled media, censorship, and strategic propaganda maneuvers.
You can check out InformNapalm for more in-depth details about the acquired intelligence.
Impact and Response
Discrepancy in Information Regarding Troop Movements
One significant revelation pertains to conflicting reports surrounding the movements of Russian troops in Ukraine’s southern Kherson region.
Information credited to the Defense Ministry, suggesting a troop withdrawal, was initially published by Russian state-run media outlets TASS and RIA Novosti.
However, these reports were swiftly retracted, with the Russian Ministry of Defense dismissing them as a “provocation” without providing further elaboration.
👀
🔥 Ukrainian hackers of the Cyber Resistance group hacked the infocommunications department of the Russian Ministry of DefenseHackers provided the international intelligence community InformNapalm with unique internal documentation and access to software used by Russian… pic.twitter.com/9nBK96iBkp
— Kvist.P 🇩🇰🇺🇦 (@kvistp) November 28, 2023
The Significance of “Regrouping” in the Conflict
Of note is the utilization of the term “regrouping” by the Kremlin to describe tactical maneuvers by Russian forces in the context of the Ukraine conflict.
The term had previously been employed to describe strategic retreats by Russian troops during the invasion.
In the wake of reports on Russian forces allegedly regrouping in Kherson, the Katyusha system reportedly collected posts on Telegram deemed critical of the Defense Ministry.
“Russia, preparing for Putin’s elections, is most likely beginning the last wave of purges of Telegram from any manifestations of disloyalty to the Kremlin,” remarked InformNapalm following the news agencies’ reports on Russian forces in Kherson.
Conclusion: Unveiling Katyusha’s Deceptive Facade
The significance of this breach cannot be overstated.
It underscores the vulnerability of critical defense systems and the potential implications of cyber espionage in an ongoing conflict.
It highlights the immense value of cybersecurity and the persistent threat posed by unauthorized access to sensitive military operations.
While these claims remain unverified and official responses are awaited, this breach serves as a stark reminder of the escalating digital warfare intertwining with geopolitical conflicts.
The revelations, if authenticated, could influence the narrative surrounding Russia’s military operations in Ukraine and prompt heightened scrutiny of its propaganda machinery.
~
As this story develops, the implications of such cyber operations will continue to unfold, necessitating thorough investigation and diplomatic responses.
The precarious intersection of cyber infiltration and geopolitical tensions demands heightened vigilance and global attention to navigate this evolving landscape of digital warfare.
—
Check out:











COMMENTS