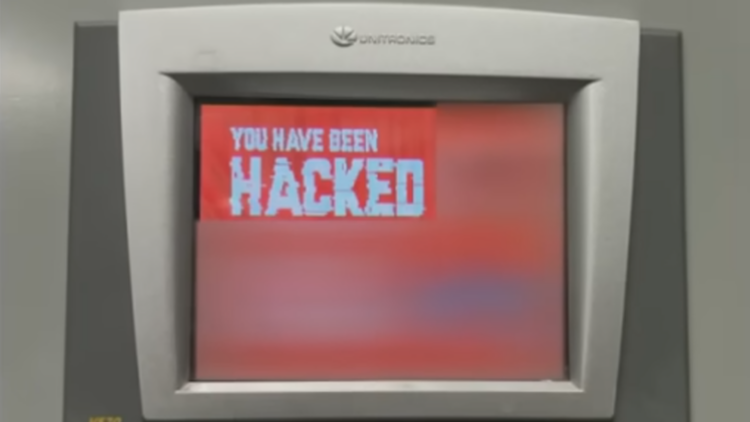
“You have been hacked, down with Israel. Every equipment ‘made in Israel‘ is CyberAv3ngers legal target,” the defacement image left by the IRGC-affiliated hackers read.
Incident Reports: Impact and Concerns
Instances of these attacks have been documented across multiple states since November, with reports confirming breaches in “less than 10” domestic water facilities, a source told CNN.
Although the attacks have not resulted in disruptions or posed threats to drinking water, the ease with which they were executed raises concerns among US officials.
IRGC’s Involvement
Federal agencies attribute these cyber intrusions to IRGC-affiliated actors, signaling the IRGC’s involvement in cyber warfare.
The IRGC, a branch of the Iranian military designated as a foreign terrorist organization by the US State Department, maintains an external operations force known as the IRGC-Qods Force (IRGC-QF), responsible for covert and terrorist operations beyond Iran’s borders.
The tactics employed by the IRGC-QF extend to targeting US, Israeli, Saudi, and UAE interests, demonstrating their capability to conduct covert and lethal activities globally.
These actions align with Iran’s strategic use of terrorism to assert influence, support allies, and project power within the Middle East region.
Urgent Need for Protection
Moreover, the recent cyberattacks on US water facilities have brought attention to the vulnerabilities within critical infrastructure.
Hackers targeted internet-connected devices with default passwords, highlighting the urgent need for enhanced cybersecurity measures, particularly securing industrial equipment linked to essential services.
Mitigation Efforts: Collaboration and Recommendations
In response to these cyber threats, federal agencies, private experts, and industry executives have mobilized efforts to mitigate risks.
The focus remains on urging organizations, especially critical infrastructure entities, to implement the recommended security measures outlined in the advisory.
This includes removing industrial equipment from public internet exposure, changing default credentials, and enhancing network security protocols.
The implications of these attacks extend beyond technological vulnerabilities; they underscore the evolving landscape of cyber threats on critical infrastructure.
The potential for cyber intrusions to disrupt essential services necessitates a proactive approach to cybersecurity, emphasizing collaboration between government agencies, private sectors, and local officials.
The agencies have observed the IRGC-affiliated activity since at least October 2023, when the actors claimed credit for the cyberattacks against Israeli PLCs on Telegram.
Since 1 November, the IRGC-affiliated actors have targeted multiple U.S.-based facilities. pic.twitter.com/u7NfKWSXe5
— Ian Ellis (@ianellisjones) December 2, 2023
The recent advisory serves as a stark reminder of the evolving nature of cyber warfare and the critical importance of bolstering defenses against such threats.
The responsibility to safeguard critical infrastructure against cyber intrusions lies not only with federal agencies but also with local authorities and industry stakeholders.
Rep. Chris Deluzio, a Democrat whose district includes the Aliquippa water authority, told CNN on Friday he received a confidential briefing on the water hack this week but declined to elaborate.
“Our adversaries don’t care who runs critical infrastructure,” Deluzio said, adding, “If they can get in through the weakest link — and [if] that’s a small municipal authority or a private vendor — that’s what they’re going to target.”
The urgency to fortify defenses and stay vigilant against emerging cyber threats remains paramount to safeguarding national security and preserving the integrity of essential services.
Conclusion: Safeguarding Critical Infrastructure
In conclusion, the CISA advisory highlighting the Iranian cyber group’s attacks on US facilities using Israeli-made systems serves as a wake-up call for bolstering cybersecurity measures across critical infrastructure sectors.
The collaboration between various agencies and stakeholders signifies the collective effort required to defend against evolving cyber threats and safeguard national interests.
This advisory underscores the imperative for proactive cybersecurity measures, collaboration, and continuous vigilance in mitigating cyber risks to ensure the resilience and security of critical infrastructure in the United States.
—
Check out:










COMMENTS